Guiding to Windows 7 security
 Windows has produced many versions of its operating system, but out of all of those windows vista is the most secure one. Windows 7 takes the base of what vista is lacking and then improves upon that to provide a secure environment. To ensure that the security features of windows vista are good, the people at Microsoft provided with a facility of user feedback to boost up their experience. Some of the security improvements which windows 7 have made in context to windows vista are as follows:
Windows has produced many versions of its operating system, but out of all of those windows vista is the most secure one. Windows 7 takes the base of what vista is lacking and then improves upon that to provide a secure environment. To ensure that the security features of windows vista are good, the people at Microsoft provided with a facility of user feedback to boost up their experience. Some of the security improvements which windows 7 have made in context to windows vista are as follows:
Core System Security
Security development life cycle (SDL) is used to develop windows 7 which were also used in the making of vista. The new operating system has all those security features which were used to protect vista such as Kernel Patch Protection, Data Execution Prevention (DEP), and Mandatory Integrity Levels. These features help to protect windows 7 and also fight against malicious software and other virus attacks.
Enhanced UAC
UAC which is also known as User Account Control was first introduced with windows vista which helped to provide authorized access and also improve the cost for granting administrator access to users. UAC was primarily developed by Microsoft with the intention to improve the coding practices for the software developers without the access to its sensitive areas of the operating system. Most people have accepted UAC as a security feature.
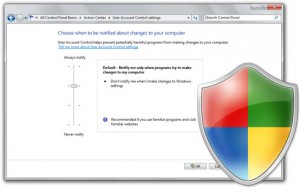
UAC is generally said to exist with the access-consent prompts. Significant improvement has been made by Microsoft to reduce the number of events that control the UAC but still it has been a great deal of negative feedback in context with the vista. In comparison to Vista, Microsoft has greatly reduced the number of applications and operating systems that trigger the prompt in Windows 7. A more flexible interface for UAC has also been incorporated in Windows 7. Now, to adjust the feature of a slider you can even change the account control settings by going under user accounts in the control panel.
There are four levels of UAC protection, and the configuration slider is used to choose among these which ranges from always notify state to never notify state. Here the always notify state helps to give you more protection. But there is an advantage of setting the slider to never notify state which is that there is only one aspect of what UAC does. No notifications are given to you under the never notify setting, and hence no UAC pop ups will ever interrupt you but some of the UAC’s core protections will still remain including protected mode internet explorer.
Integrated Fingerprint Scanner Support
In many operating systems, you can log in without using a user name and password which is same as welcoming the virus to your computer giving him a command to attack your virus. it is highly recommendable for all the users to have a strong password or a pass phrase so that only the authorized users can access your system and the tress passers would not be allowed to enter. One should keep a password which is difficult to guess otherwise someone could easily break your password protection.
Passwords are never secure and are made to be broken. Passwords are secure till the time they are not cracked, and cracking a password is like entering into the boundary walls of your enemy. Most people will suggest you to keep another protection after password protection for authentication purposes which is same as adding a layer above another layer. Now days many computers and computers come with built in security systems in the form of a fingerprint scanner. In such systems the system checks your fingerprint and allows you to access the system if it is right. Since no person expects you can have same fingerprint, no space is left for anyone to access your system. Windows 7 is now provided with more integration between the operating system and the finger print scanning device.
Windows 7 has got much better driver support and more reliable fingerprint reading hardware across different hardware platforms. Using a fingerprint reader with Windows 7 for accessing to Windows 7 and to access other applications and web services is easy. To use these hardware devices, you can click on the control panel to access it and manage the fingerprint data and security settings.
If any biometric devices are connected to the system, then the biometric device console will interrupt to let you know about that. ‘Not enrolled’ is the message which will be displayed if the fingerprint reader is not recognized and to access the console you can then click on that status message.
To your fingerprint database, you can add scans of one finger or all ten. This facility of storing the fingerprint of more than one finger gives you the facility of using your other fingers even if one of your fingers is damaged or if you cannot use your finger due to injury. You just need to place your finger on the fingerprint reader, it depends upon the hardware you are using, and it will read it to save it in its database. Your each finger is scanned three times in order to confirm it from the database. It is similar to reenter a password to confirm if you have entered it correctly.
Protecting Data
Each year thousands of laptops are stolen, so you need to have some mechanism in order to protect them. If you don’t have appropriate security controls in place, any unauthorized user can easily access your system along with your sensitive data if any. With USB flash drives and other removable devices used, the risk of sensitive information being lost or stolen increases to a great extent. USB’s can save a lot of data; you may not even get aware of what the other person is taking from your system.
Technologies which are used in Windows Vista such as EFS (Encrypting File System) and support for AD RMS (Active Directory Rights Management Services) are now also incorporated in Windows 7. Windows 7 greatly improves Bit Locker which is used in Vista as an encryption technology, which can be used to encrypt data on removable media.
Encrypting Drives with Bit Locker
Initially at the time of introduction of Bit Locker with Windows Vista, it was only capable of encrypting the primary volume of the operating system. The functionality to encrypt other volumes with Windows Vista Service Pack 2 such as more drives or partitions on the hard drive has improved but to encrypt the data on portable or removable disks is still not possible. Windows 7 brings you the facility of Bit Locker to protect the data on removable drives along with providing a leans of sharing the data with other people.
The disk volumes need to be configured properly before you begin using Bit Locker drive encryption. A small unencrypted partition is needed by windows to contain the core systems which it needs to boot process and for authentication of the users to access the encrypted volumes. While setting up the drive manually, people don’t consider it many a times, so Microsoft has created a tool for Bit Locker drive partition which can be easily downloaded from the Microsoft’s site.
You can encrypt the files using Bit Locker as soon as you are able to properly partition them. First step is to click on the Bit Locker drive encryption in the control panel which will then display the user interface of all the available drives and their current states, indicating whether Bit Lock is protecting them or not. The display then separates the drives according to whether they are fixed drives or removable drives to be protected by Bit Locker.
To now begin the encryption process, you need to turn on the Bit Locker by clicking on it. The interface then asks from you a password for unlocking the encrypted data, or you can even insert your smartcard for authentication purposes. An opportunity is provided to you by the Bit Locker to save the recovery key either as a text file or in a printed format. You must have this recovery key to unlock the data in case you forget your password or of the authentication fails.
This tool helps to encrypt the data in the background, while at the same time you can use the windows normally. After the encryption process is completed, you need to click on the Manage Bit Lock and then choose to unlock your encrypted drives automatically when you log on to the windows.
Using Bit Locker without a TPM
Bit Locker often requires a TPM (Trusted Platform Module) chip in the default case, which is used to store the encryption keys to facilitate the encryption and decryption of the protected data of Bit Locker. Mostly laptops and computers are not having TPM chips, exceptions are always there.
Microsoft has now included the option for encryption purposes without using a TPM, but accessing the option is not easy at all. Following steps should be taken to use a Bit.
Locker without a TPM chip in it:
- On the button left side of the screen, click the Windows logo.
- Go to ‘search program and files’ at the bottom of the start menu, then type gpedit.msc and press enter.
- Now go to administrative templates, windows components, and various drives under computer configuration.
- Double click on the authentication at the startup option.
- Select the radio button at the top and then check the allow Bit Locker without a TPM check box.
- Click OK.
Protecting Mobile Data with Bit Locker to Go
Windows Vista has always been unable to encrypt the data on removable drives but was able to protect the drives and volumes which are a part of the computer. Windows 7 has now got this functionality to go.
During the encryption process, you must not remove it from he removable drive as a it can lead to loss of data. If you do this before the completion of the encryption process, you drive may get damaged. In order to protect your drive, you can use the option of the pause button which halts the process for a particular time.
With Bit Locker you can protect the data from the removable drives. If you need to share some kind of sensitive information with other people, then you can encrypt the data on the USB drive and also choose a password that you can share with them to unlock the events. It is same as that of providing the key when connecting Bluetooth devices.
To protect the data of the removable drives, Bit Locker gives you this ability to control it. With the group policy, the administrators make unprotected removable storage read only which can then require that the system applies the encryption process to the removable storage before users can save data on it.
